Identify Risks Before Damage Occurs
Vulnerability Management with SBOM
Secure your software supply chain with SBOM
With a Software Bill of Materials (SBOM) and vulnerability management, you detect weaknesses early and manage risks proactively.
Imagine you read about a software vulnerability in a widely used component, but you don’t know whether that component is included in your systems. You need to act—and fast.
Shortly afterward, one of your service providers informs you: two of their applications are unaffected, but a third (which you also use) is vulnerable—and urgently needs an update.
How could the provider act so quickly? Because they employed an SBOM and robust dependency tracking. They identified the CVE the day before, patched the affected component proactively, and neutralized the potential risk before it escalated.
This could be your next success story - thanks to the SBOM and conplement as your software partner.
Legal framework
The legal and regulatory context for SBOMs in Germany is shaped by BSI (Federal Office for Information Security) recommendations and the EU Cyber Resilience Act (CRA).
-
BSI guidelines
The BSI’s technical guideline TR-03183-2 defines formal and technical requirements for SBOMs. It aims to increase supply chain transparency around third-party software components, helping manufacturers and users monitor vulnerabilities.
-
Cyber Resilience Act (CRA)
Deployed in Europe three years after its adoption (i.e. as of February 2027 in Germany), the CRA mandates that manufacturers document software components to prove their products do not contain known vulnerabilities. The CRA’s requirements align with BSI guidelines and are part of a broader push toward uniform cybersecurity practices across the EU.
-
Challenges
Implementing SBOMs in compliance with BSI rules requires significant organizational change: adapting software development processes, forming cross-disciplinary teams (compliance, product, procurement), and embedding SBOM responsibility in your workflows. At conplement AG, we already support clients in precisely this transformation - with mature methodologies and experience.
Security by design: SBOM’s role in vulnerability analysis & compliance
The SBOM should ideally be generated in parallel with the software itself and directly feed vulnerability analyses of software components. That’s typically done within CI/CD pipelines, ensuring the SBOM stays up to date and reflects all changes.
Each released software version should be accompanied by its own SBOM so that every variant in the field can be traced. This also aligns with CRA expectations that software producers know which third-party components their products contain.
"…For manufacturers, it is particularly important to ensure that their products do not include vulnerable components developed by third parties."
Dependency Tracking
Our approach: continuous, real-time SBOM analysis
Our dependency tracking solution continuously analyzes SBOMs in real time. Designed for seamless integration with modern CI/CD pipelines, it automatically spots security issues early. You gain full visibility across all projects, identify affected components immediately, and respond in a targeted way.
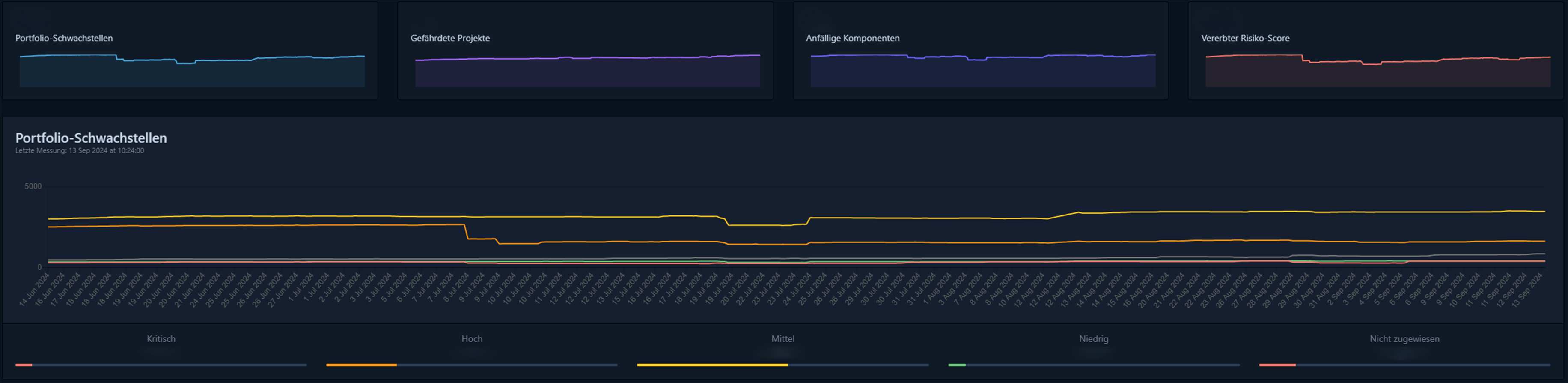
Dependency Tracking Dashboard
Business benefits
-
Continuous integration
Because analysis is fast, our platform fits into high-velocity build pipelines. You stay ahead, catching potential issues as you develop. -
Deep insights
Understand which parts of your assets and applications are exposed. Our solution helps you rapidly spot and act on vulnerable components. -
Continuous transparency
Maintain a full inventory of all software components - far beyond what traditional tools offer. Optionally, you can share SBOMs with others in your supply chain to strengthen security network-wide. -
Complete stack overview
From libraries and frameworks to underlying OS and hardware, our dependency tracking offers precise visibility of used components. -
Rapid vulnerability identification and remediation
We aggregate data from multiple vulnerability sources and spotlight at-risk components so you can act quickly.
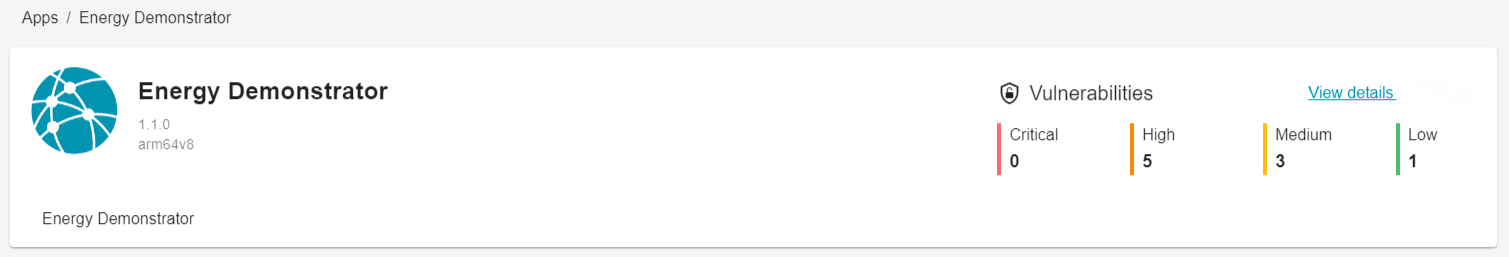
Vulnerability Dashboard in omnect Device Management
Platform features that make the difference
With the right platform for vulnerability management, potential issues can be prevented before they even arise - and that’s exactly where our dependency tracking, supported by the Software Bill of Materials (SBOM), comes into play. It offers a wide range of features that truly make the difference:
-
Seamless integration with leading vulnerability databases enables a proactive security strategy.
-
Policy evaluation ensures your projects always comply with applicable security, operational, and licensing requirements.
-
Impact analysis allows vulnerabilities to be quickly identified and remediated, while exploit prediction helps set priorities based on predictive models.
Thanks to an efficient auditing workflow, you always maintain visibility of decisions and their documentation. Automatic outdated version detection identifies obsolete components and supports timely updates. A full-stack inventory enables complete traceability of all components in your portfolio.
The platform generates and supports CycloneDX SBOMs - an OWASP standard explicitly referenced in BSI TR-03183-2 - and provides consolidated reporting of all vulnerabilities through vulnerability aggregation.
Our dependency tracking not only meets but exceeds official security requirements such as NIST VDR and CISA VEX, and through automated notifications integrates seamlessly with common collaboration tools. Enterprise-ready features like SSO, Active Directory support, and an extensive API for easy system integration make our dependency tracking the optimal choice for companies.
In addition, the platform offers time-series metrics to track the progression of risks and compliance violations in detail. As an open-source solution under the Apache 2.0 license, you also benefit from an active community that drives continuous improvement and development of the platform.
Use in conplement AG projects
In all our client projects - and in our own solutions - we adhere to “Security by Design.” We generate SBOMs automatically within CI/CD and integrate them into our dependency tracking platform. This allows developers to be alerted immediately to issues and provide fast updates.
For example, we link security findings to Azure DevOps, or other platforms, tailoring the integration to your setup. We also offer full security assessments, such as Threat Risk Assessments (TRA), using our proprietary Security Canvas (inspired by the Business Model Canvas) for a holistic view of security.
Start with our Security Canvas
In both our own products (omnect and twinsphere) as well as in customer projects, we strictly rely on the creation of an SBOM, which is automatically generated within the CI/CD (Continuous Integration / Continuous Delivery) process and integrated into a dependency tracking platform. This ensures that developers are immediately alerted to issues and can respond quickly by providing updates.
The “Security by Design” approach is also embedded in omnect Secure OS, our secure managed Linux OS designed specifically for manufacturers of edge devices and component producers. It ensures continuous operation, strong security, and compliance with relevant regulations. This secure Linux meets the requirements of a modern embedded Linux, powered by conplement AG’s state-of-the-art technology.

Thomas Wahle
Vorstand

Britta Waligora
Vorstand

Christian Günther
Innovation & Portfolio Architect, TOPIC OWNER Digital Twin



